Key Takeaways:
A crypto consumer misplaced almost $50 million in USDT after copying a spoofed pockets tackle from transaction historical past.The assault used tackle poisoning, exploiting pockets interfaces that disguise the center of addresses.Funds have been shortly swapped and routed by way of a number of wallets, with parts despatched to Twister Money, limiting restoration choices.
A single copy-paste mistake has resulted in probably the most costly consumer errors ever recorded on-chain. The incident highlights how easy interface habits can override in any other case cautious habits and result in irreversible losses.
How a Routine Check Switch Turned Right into a $50M Loss
In response to on-chain investigators, together with Lookonchain, the sufferer started with a step many skilled customers think about finest follow: a small check transaction. The consumer despatched 50 USDT to a well-recognized private pockets tackle to verify accuracy earlier than shifting a a lot bigger quantity.
That check switch, nevertheless, grew to become the set off.
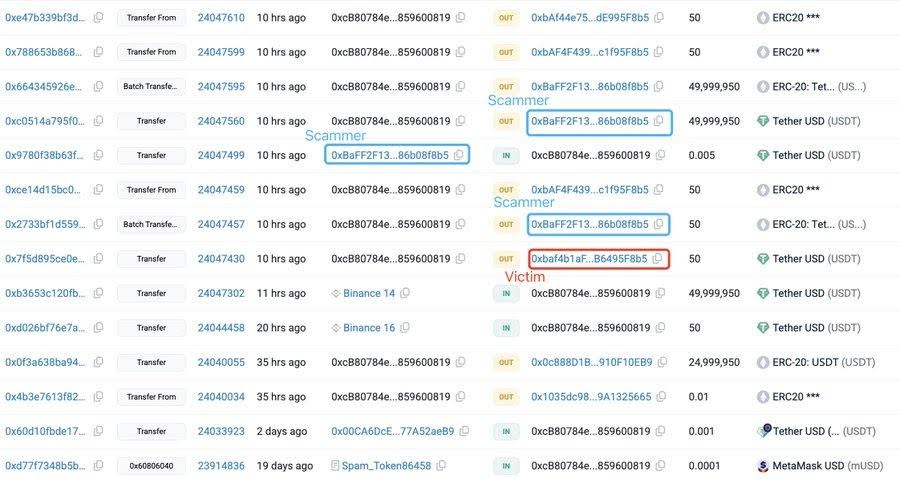
Inside moments, a scammer deployed an tackle poisoning tactic. The attacker created a pockets tackle, which had the identical first, and final 4 digits as the real tackle of the sufferer. A small transaction was then despatched to the sufferer on this tackle which regarded as the actual one, ensuring that it could be recorded within the pockets of the transaction historical past.
When the sufferer returned to finish the principle switch: 49,999,950 USDT, they copied the tackle from transaction historical past somewhat than the unique saved supply. As a result of many pockets interfaces truncate addresses with “…”, the pretend tackle appeared official at a look. The cash was transferred directly and completely to the hacker.
Learn Extra: Pi Community Flags Rip-off Pockets Amid $346M Token Dangers as 60M Customers Await Unlock


Handle Poisoning: A Low-Tech Assault With Excessive Influence
There is no such thing as a have to hack private keys or to make using sensible contracts. It’s depending on human interface and habits.
Why This Assault Nonetheless Works at Scale
Most wallets abbreviate addresses with the intention to improve readability. Transfers are steadily checked by the consumer by checking the primary and the final tackle. That is abused by attackers who generate addresses that mirror such seen characters.
On this occasion, the scammer did this instantly after the check transaction and it signifies computerized monitoring. The attacker made comfort disguise a greater purpose to take warning by putting a near-identical tackle within the historical past of transactions of the sufferer.
This methodology is taken into account fundamental in contrast with advanced DeFi exploits. But the result exhibits that even “easy” scams can produce catastrophic losses when giant sums are concerned.
On-Chain Actions After the Theft
Blockchain data present that the stolen USDT didn’t stay idle. The attacker very swiftly exchanged the a part of the funds to ETH and despatched them to a number of wallets, which is typical to decrease the traceability.

The property have been later transferred to Twister Money, a privateness mixer that hides the paths of transfers. As quickly as the cash is invested in such companies, restoration is extraordinarily unlikely with out a right away motion of the exchanges or validators.
The chain of wallets was described by analysts who claimed it was environment friendly and preplanned that means the scammer was all set to make an motion as quickly as the massive switch was made.
Why This Case Shocked Analysts
Handle poisoning is broadly identified and infrequently mentioned as a nuisance rip-off involving small quantities. What makes this case stand out is the scale and the profile of the error.
The sufferer adopted a standard security step by testing with a small switch. Mockingly, that motion gave the attacker the sign wanted to deploy the spoofed tackle at precisely the fitting second.
On-chain observers famous that simply seconds spent copying the tackle from the unique supply, somewhat than transaction historical past would have prevented the loss fully. The velocity of blockchain finality left no window for reversal.
Learn Extra: Shenzhen Points Crypto Fraud Alert as Stablecoin Scams Multiply Throughout China
Pockets Design and the Human Issue
This incident raises questions on pockets UX selections. Truncated addresses enhance visible readability however cut back safety for customers dealing with giant sums.
Some wallets now warn customers about tackle poisoning or flag addresses that intently resemble identified ones. Others supply tackle whitelisting, the place transfers are restricted to pre-approved addresses. Adoption of those options, nevertheless, stays inconsistent.
Support Greater and Subscribe to view content
This is premium stuff. Subscribe to read the entire article.














