Key Takeaways:
Ledger confirmed a buyer knowledge publicity tied to its third-party cost processor, World-e.Leaked data consists of names and speak to particulars; no pockets seeds, personal keys, or crypto funds have been compromised.The incident was first flagged publicly by blockchain investigator ZachXBT, prompting buyer notifications and an ongoing forensic assessment.
Ledger customers obtained an alert after World-e detected unauthorized entry inside components of its cloud techniques. The disclosure renews scrutiny on third-party threat in crypto commerce, even when core pockets infrastructure stays intact.
What Occurred: Third-Celebration Publicity, Not a Pockets Hack
Ledger disclosed that the incident occurred exterior its personal {hardware}, software program, and platform setting. The breach traces again to World-e, which serves as a merchant-of-record and cost processor for Ledger’s on-line retailer.

In line with the notification despatched to prospects, World-e recognized uncommon exercise and rapidly carried out controls. An impartial forensic investigation later confirmed that some buyer order knowledge was improperly accessed. The uncovered fields embrace names and different contact data, whereas cost particulars weren’t concerned.
Ledger emphasised a vital level for customers: World-e doesn’t have entry to restoration phrases, personal keys, balances, or any secrets and techniques tied to self-custodied property. Because of this, the publicity doesn’t have an effect on the cryptographic safety of Ledger gadgets.


What Information Was Uncovered and What Was Not
There must be a definite line in such incidents. The info can be found to point out a knowledge privateness incident, however not a crypto compromise.
Uncovered
Buyer namesContact particulars related to orders (corresponding to electronic mail or transport data)
Not uncovered
Restoration phrases (24 phrases)Personal keys or pockets secrets and techniquesOn-chain balances or transaction signingCost card knowledge
This identification restricts the publicity to direct monetary threat, though the opportunity of focused phishing is larger. Hackers can use knowledge that has been leaked to design persuasive messages that fake to be the work of pockets suppliers.
Self-Custody Limits the Blast Radius of Information Leaks
The self-custodial mannequin that’s utilized by Ledger served as a really strict border. Attackers had no avenue to empty funds or make transactions, even within the presence of third-party order data. The risk modifications to social engineering slightly than stealing property and vigilance is the main line of protection.
How the Incident Got here to Mild
The matter got here into the limelight when ZachXBT posted a neighborhood alert on X, which cited the emails given by prospects who detailed in regards to the World-e breach. Disclosures like these have a tendency to hurry up the creation of consciousness in that they combine on-chain tradition and off-chain safety reporting.
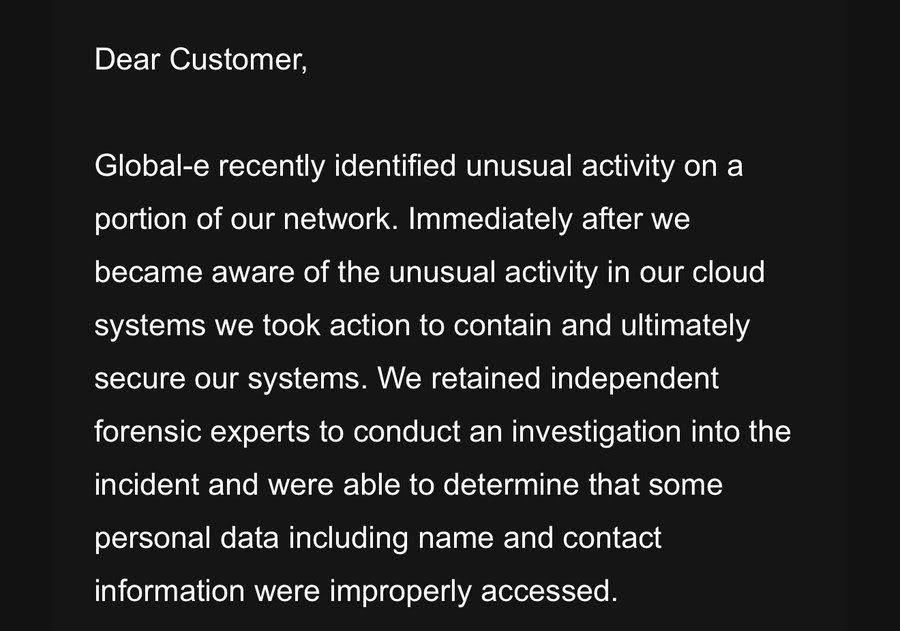

Quickly sufficient, Ledger took cost of the incident and sorted out obligations. World-e is the info controller of the order processing; subsequently, it took the initiative of notifying prospects. Ledger coordinated communications in order that the customers have been conscious of the extent and limits of the publicity.
The next separation of roles is frequent to the ecommerce trade, and it demonstrates a constant risk to crypto firms that have to be exterior processors to cater to worldwide markets.
Learn Extra: BNB Chain Brings on High Crypto Sleuth ZachXBT in Main Push to Fight Web3 Scams and Fraud
Why Third-Celebration Danger Retains Hitting Crypto Manufacturers
Crypto companies are relying increasingly more on devoted distributors in areas like cost, logistics and compliance. Each integrations improve the assault floor of the pockets or protocol itself.
The case of Ledger is an element of a bigger tendency:
Support Greater and Subscribe to view content
This is premium stuff. Subscribe to read the entire article.














